Advanced Computing, Mathematics and Data
Research Highlights
October 2015
Taking Action for Resilient Cyber Systems
Demo and workshop paper to showcase novel graph model at ACM Conference on Computer and Communications Security
As part of this year’s 22nd ACM Conference on Computer and Communications Security, a Pacific Northwest National Laboratory-led team will present a workshop paper and a demonstration—Action Recommendation for Cyber Resilience—that showcase the advantages of using a graph-based approach for reasoning about system resiliency. The work aims to mitigate targeted cyber attacks that can disastrously impede proper operations of computing services and systems.
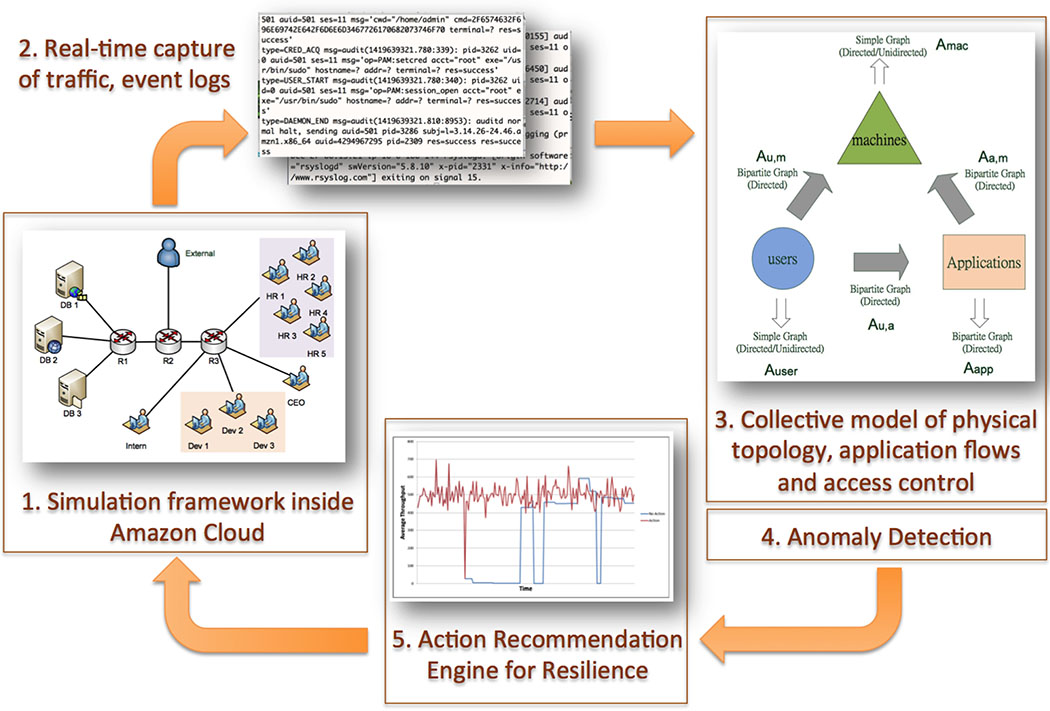
Demonstration of the recommendation workflow. (1) A test system is dynamically started inside Amazon Cloud. (2) The test framework collects network traffic and various logs from each virtual machine that is started and pushes data to a cloud storage system. (3) Another machine inside Amazon Cloud continuously runs a monitoring system, pulling data from cloud storage and building a model. (4) Next, it performs anomaly detection and, in the event of an anomaly, (5) makes a recommendation to the system defender. Currently, recommendations include decisions to stop or migrate a service or block communication between two machines. The team is working on expanding the recommendations to more sophisticated actions that include fine-grained user access control and strategic hardening of selected machines. Enlarge Image.
In experiments, the graph model demonstrated it could represent the infrastructure, behavior, and missions of a cyber enterprise, or the elaborate web of applications, software, storage, and networking hardware. In the paper describing the formal method for their model approach, scientists from PNNL, the University of Michigan, and Colorado State University also explained how metrics computed from the model were used to implement an algorithm for recommending resilience-establishing actions.
According to Sutanay Choudhury, a research scientist with PNNL’s Advanced Computing, Mathematics, and Data Division Data Sciences group and principal investigator of the project that facilitated this research, representing a cyber enterprise using the unifying graph-based model has “big appeal” possibilities.
“The model allows for ingesting multiple data sources, such as network flow, event logs, vulnerability information etc., into one model. Then, we can reason about actions in the model space before employing transformed actions that were determined in that space,” he said. “For example, deleting a graph edge in the model space may be akin to blocking rogue communication between a client and a server in the real world.”
The demonstration, to be presented at ACM CCS 2015 by PNNL’s Luke Rodriguez (also from the Data Sciences group), will model the cyber enterprise of a fictional small e-commerce company (VISR) in both a software simulation, for scenario testing, and inside Amazon Cloud (also known as Amazon Web Services or AWS), for seeing how the model theory interacts with reality. Notably, while many PNNL projects employ cloud computing for operational reasons or engineering, this cyber security work also represents PNNL’s initial foray into cloud-focused research. Ultimately, the goal is to represent the graph model’s ability to detect and respond to cyber-attack threats in real time in both the software and Amazon Cloud simulation frameworks. The code developed by this project also will be released as open-source software via GitHub.
While actual mapping of theoretical models of cyber attacks to real-world scenarios still is forthcoming, Choudhury is very excited by the first steps his team has taken to analyze the resiliency of a complex enterprise web in a meaningful way.
“As a team, we really went in circles again and again on resilience research and what was worth developing theory and experiments around,” he explained. “I am really glad because this work gives us a foothold to rise from.”
The research for both the demonstration and the paper is supported by PNNL’s Asymmetric Resilient Cybersecurity Initiative, which includes a diverse team of computer scientists and mathematicians from PNNL’s Physical and Computational Sciences and National Security directorates.
ACM CCS 2015 is the flagship annual conference for the Association for Computing Machinery’s Special Interest Group on Security, Audit and Control (SIGSAC). The conference is being held in Denver on October 12-16, 2015.
Research team: Sutanay Choudhury, Luke Rodriguez, Darren Curtis, Kiri Oler, and Peter Nordquist (PNNL); Pin-Yu Chen (University of Michigan); and Indrajit Ray (Colorado State University).
References:
- Choudhury S, L Rodriguez, D Curtis, K Oler, P Nordquist, P-Y Chen, and I Ray. 2015. “Action Recommendation for Cyber Resilience.” Workshop on Automated Decision Making for Active Cyber Defense (SafeConfig 2015). October 12, 2015, Denver, Colorado (held in conjunction with ACM CCS 2015).
- Rodriguez L, D Curtis, S Choudhury, K Oler, P Nordquist, P-Y Chen, and I Ray. 2015. “Demo: Action Recommendation for Cyber Resilience.” ACM Conference on Computer and Communications Security (ACM CCS 2015). October 12-16, 2015, Denver, Colorado.
